LOKI Product Datasheet
Adding cost on the Adversary
Creating Uncertainty
Disrupting the Kill Chain
Portfolio Overview
GhostGrid
Deploy an entire network of traps systems that replicate network services to create realistic decoy networks that mislead and catch attackers.
Code Ambusher
Code-level traps that embed well-crafted lures into application code with real-time monitoring and forensic analysis capabilities.
Deception Lures
Strategic tokenized objects with AI-powered content generation and detailed tracking capabilities that catch attackers in action across multiple file types.
Social Deception
Comprehensive awareness platform that combines fake user profiles, communication monitoring, and training integration to detect and prevent social engineering attacks.
Deception is one of the 14 techniques to deploy a cyber resilience
Use deception to confuse and mislead adversaries regarding the information they use for decision-making
Modern defense requires actively engaging and manipulating the adversary's perception of the environment
LOKI Architecture
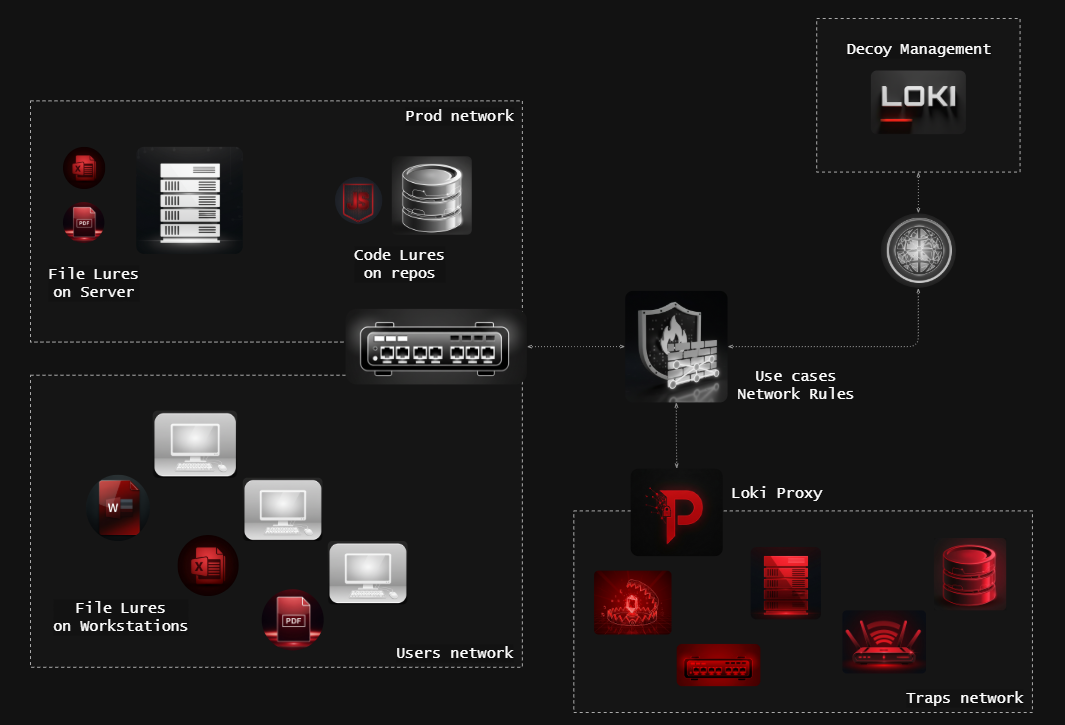
About LOKI
LOKI is a cutting-edge cybersecurity company specializing in deception technology that transforms traditional defense strategies. Our platform creates sophisticated traps and lures that deceive attackers, providing organizations with advanced threat detection and intelligence gathering capabilities.
Founded in 2025, LOKI has quickly established itself as a leader in the deception technology space, serving Fortune 500 companies, government agencies, and organizations across various industries worldwide.
Our mission is to turn the tables on cyber attackers by using their own tactics against them, providing defenders with the tools they need to detect, analyze, and neutralize threats before they cause damage.
GhostGrid
Technical Specifications
- Virtual Assets1000+ per deployment
- Network ProtocolsTCP/UDP/ICMP
- Service Emulation50+ services
- ScalabilityUnlimited nodes
- Response Time< 100ms
System Requirements
- CPU2+ cores
- RAM4GB minimum
- Storage100GB
- Network1Gbps recommended
Infrastructure Support
- VirtualizationVMware, Hyper-V, KVM
- Cloud PlatformsAWS, Azure, GCP
- Container SupportDocker, Kubernetes
- Network TypesLAN, WAN, DMZ
Network Mapping
Automatically discovers and replicates network services
Service Fingerprinting
Creates realistic services for enhanced deception
Traffic Analysis
Packet and log inspection and behavioral analysis
Threat Correlation
Cross-platform threat intelligence correlation
Primary Use Cases
Network Security
Create decoy networks to mislead and trap attackers
Lateral Movement Detection
Detect attackers moving through network infrastructure
Threat Intelligence
Gather detailed intelligence on attacker tools and techniques
Code Ambusher
Technical Specifications
- DeploymentCloud/On-Premise
- Languages Supported10+ Programming Languages
- IntegrationCI/CD Pipeline Ready
- Detection Time< 5 seconds
- False Positive Rate< 0.1%
Intelligent Code Injection
Embeds well-crafted lures into application code
Real-time Monitoring
Continuous check of lure interactions and suspicious activities
Dynamic Response
Adaptive controls based on attacker behavior patterns
Forensic Analysis
Attack vector analysis and threat intelligence gathering
Primary Use Cases
Early Breach Detection
Use decoy code snippets to detect intrusions before real damage occurs.
Insider Threat Monitoring
Plant decoy code in restricted areas to catch insider misuse.
Data Exfiltration Traps
Track code to identify exfiltration attempts.
Compromised System Identification
Use decoy systems to detect scans or lateral movement.
Supply Chain Security Monitoring
Embed lures in code to catch supply chain breaches.
Deception Lures
File Types Supported
- DocumentsPDF, DOC, XLS, PPT
- ImagesJPG, PNG, GIF, TIFF
- ArchivesZIP, RAR, 7Z
- ScriptsPS1, BAT, SH
- Custom FormatsAPI extensible
Tracking Features
- Access LoggingDetailed file interactions
- Copy DetectionUnauthorized duplication
- Print MonitoringPhysical access tracking
- Network TraversalCross-system movement
- Forensic MarkersSteganographic watermarks
Content Generation
AI-powered creation of realistic document content
Distribution Management
Strategic placement across file systems and networks
Chain of Custody
Detailed tracking of file access and movement
DLP Integration
Enhanced data loss prevention with active monitoring
Primary Use Cases
Data Loss Prevention
Monitor and prevent unauthorized data access
Intellectual Property Protection
Safeguard sensitive corporate documents and research
Compliance Monitoring
Ensure regulatory compliance for sensitive data handling
Social Deception
Profile Generation
- User PersonasAI-generated profiles
- Social Platforms5+ platforms
- Communication StylesDepartment-specific
- Activity SimulationRealistic usage patterns
Detection Mechanisms
- Login MonitoringReal-time alerts
- Message TrackingEmail/Chat/SMS
- Social EngineeringPattern recognition
- Phishing DetectionAdvanced algorithms
Persona Management
Comprehensive fake identity creation and management
Social Graph Mapping
Understand organizational relationships and communication patterns
Phishing Campaign Detection
Early warning system for targeted social engineering attacks
Training Integration
Seamlessly integrate with security awareness training programs
Primary Use Cases
Phishing Prevention
Detect and block targeted phishing campaigns
Social Engineering Defense
Identify manipulation attempts through social channels
Executive Protection
Protect high-value targets from sophisticated social attacks
Web Trapper
Web Technologies
- Frameworks20+ popular frameworks
- CMS PlatformsWordPress, Drupal, etc.
- E-commerceShopify, Magento
- Custom ApplicationsTemplate-based creation
- API EndpointsREST/GraphQL/SOAP
Security Features
- SSL/TLS SupportAutomatic certificates
- AuthenticationMultiple schemes
- Session ManagementStateful interactions
- Vulnerability EmulationControlled exposure
- Traffic AnalysisDeep inspection
Application Cloning
Replicate existing web applications with high fidelity
Interactive Honeypots
Fully functional decoy applications that engage attackers
Attack Surface Mapping
Identify and monitor potential entry points
Primary Use Cases
Web Application Security
Protect web-facing applications from attacks
API Protection
Monitor and secure API endpoints
Zero-Day Discovery
Identify previously unknown web vulnerabilities
Contact Information
Ready to transform your cybersecurity strategy? Get in touch with our experts.